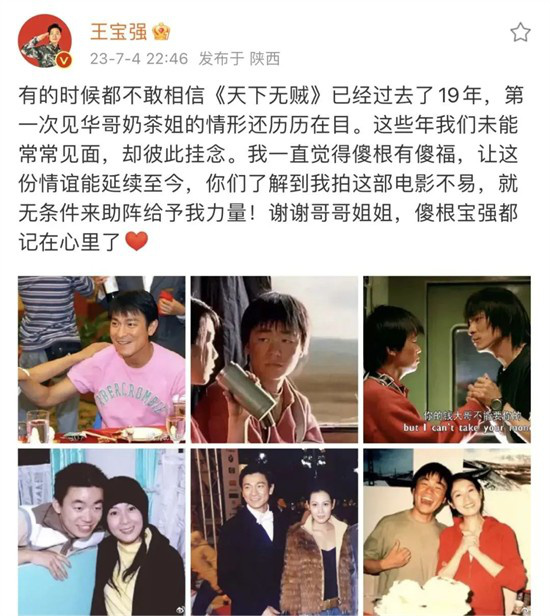
Article 24 of the Marriage Law is disputed by many judges: it is a legal error at the national level.
Shortly after Wang Jinlan’s divorce, the person who sent the subpoena to the court came to visit. She suddenly became the defendant who owed money.
Her parents are farmers and can’t read. Seeing the uniform of the court, they thought their daughter had broken some law.
Wang Jinlan, who received the summons, called angrily to question her ex-husband. The ex-husband did not hide it, admitting that he had helped his father borrow more than 3 million yuan.
Wang Jinlan, 29, didn’t realize the seriousness of the problem. "I didn’t know and didn’t spend the money they borrowed. The lawsuit will definitely win." She didn’t even appear in court and left everything to her lawyer.
After the verdict came down, she lost and needed to share the debt. The sentence reads "Article 24 of the Supreme People’s Court’s Interpretation on Several Issues Concerning the Application of the Marriage Law of the People’s Republic of China (II)".
This judicial interpretation came into force on April 1, 2004. "Article 24" is short in words: "Where a creditor claims rights for debts incurred by one spouse in his own name during the marriage relationship, it shall be treated as joint debts of the husband and wife. However, unless one of the spouses can prove that the creditor and the debtor have clearly agreed to be personal debts, or can prove that it belongs to the circumstances stipulated in the third paragraph of Article 19 of the Marriage Law. "
Now Wang Jinlan knows that these two sentences mean that if a spouse plays an iou outside behind his back, even if he doesn’t know it, the law may hold her responsible because of the relationship between husband and wife.
It was not until she entered a WeChat group called "Twenty-four Public Welfare Groups" that Wang Jinlan discovered that it was not only herself, but anyone could encounter "Twenty-four Articles".
In contrast, Wang Jinlan feels that his tragic and bizarre experience is simply "dwarfed."
After a judge in Wenzhou used Article 24 to sentence others, he lost the case because of Article 24 and moved into a private house with a monthly rent of 800 yuan. A group of friends in Yunnan haven’t eaten a bite of meat for 4 months, so they can only go to the vegetable market to pick the remaining leaves at night; A primary school teacher in Jinan goes to a snack bar to earn money in winter and summer vacations, and wears a hat and mask at work for fear of being recognized. A group friend in Hangzhou, whose medical insurance card was seized, suffered from breast cancer and had to borrow money for surgery … …
"Marriage is risky, so divorce should be cautious."
Those in the group who are in the same boat as Wang Jinlan include civil servants, teachers, journalists and employees of state-owned enterprises … … Their common experience is obvious: because of Article 24, they are passively in debt, entangled in lawsuits, their salary accounts are frozen, and they are listed as "untrustworthy executors" by the court, with debts ranging from tens of thousands to ten million yuan.
A real-name questionnaire survey of 527 members conducted by Peng Yun, Li Xiuping and others shows that 87.1% of the group members are women and 80.6% have received higher education. More than half of the people said that their lawsuit involved more than 1 million yuan.
Searching for the keyword "Article 24 of the Supreme People’s Court’s Interpretation on Several Issues Concerning the Application of the Marriage Law of the People’s Republic of China (II)" in China’s judgment documents online, as many as 81,288 judgments appeared. In 2016 alone, 30,484 copies were added.
In May last year, Wang Jinlan published an article in her Weibo, "Marriage is risky, so divorce should be cautious". The number of hits of the article reached 6.5 million.
In the blog post, she posted her wedding photos and warned everyone that if she decided to get married, she must first study the Marriage Law, especially the judicial interpretation of Article 24.
"Once you marry the wrong person, marriage can bury your life. The price of this mistake is huge, and you may not be able to get out of the predicament all your life. " She wrote this.
Before marriage, Wang Jinlan had fantasies about marriage: having a "comfortable" and "long-lasting" love, having a lovely child and living a warm life, "not afraid of boredom and getting old".
But after a failed marriage, she deleted all the past photos in her WeChat circle of friends, afraid to mention that she was a single mother, afraid to explain to people over and over again why she was always alone.
She is more worried about how she and her children can raise their heads in case she becomes an "old lai" recognized by the court.
Insomnia, Wang Jinlan shouted in Chang Zaixin: Why me, who will help me?
When the trouble happens, many people will start by condemning themselves: Why did I meet the "scum"? Liang Nvzhu is like this.
After her ex-husband owed 5 million yuan and became "into thin air", Liang Nvzhu’s first reaction was "crying".
She drove alone to a small lake in Foshan, Guangdong Province, and cried from day to night for eight hours. College students found her and sent her home. Mother smiled and said to her, "It’s good to come back", but as soon as her voice fell, she began to cry.
At that time, Liang Nvzhu was afraid of receiving strange phone calls and express delivery, and she trembled when she saw the blue mail cover — — That usually represents the arrival of a subpoena. Every time she receives a summons, she will hide in the house and cry.
Her father sold two houses for providing for the aged, and each family came to pay back the money. Liang Nvzhu told her father more than once, "We don’t know when we borrow money, and it’s useless. Don’t pay back." But the father replied that all the borrowers lent money to her ex-husband because they knew them.
Once, at 11 o’clock in the middle of the night, someone shouted for money with a drunken cavity and a brick outside the door. My 70-year-old father rushed out with a kitchen knife and said, "whoever comes in will be hacked to death!" "
Liang Nvzhu suddenly suppressed her tears at that moment. "I can’t be weak anymore. I want to protect my family. "
After that, when someone satirizes her "Who told you to meet scum", Liang Nvzhu will reply to each other like this: I hope your daughter will not meet scum.
Refuse to surrender to fate
The core wish of these people is to abolish Article 24.
Those who are in debt because of Article 24 are not without success, but they are very few. In a coffee shop near Wudaokou, Li Xiuping quickly took out a color printed investigation report from his green computer bag, pointed to the small print in red on one page and said, "Only 1.8% of the cases of 335 people in the group who entered the execution stage have been overturned."
In her view, there is no way to solve the frequent problems of "victims" by changing the case. "After all, the person who successfully got rid of the problem debt ‘ Rare ’ " .
Li Xiuping is one of the initiators of "Article 24 Public Welfare Group" and the drafter of group regulations. They call it "core values".
Before joining the group, all newcomers are required to read the group rules, such as "This group is firmly opposed to using the image of Qin Xianglian who stops the sedan chair to complain about the group victims".
When someone blindly asks for a solution to their case in the group, she will bluntly criticize: "Encounter ‘ Liabilities ’ It’s not your fault, but you still don’t want to study and wait for a miracle, and continue to be ignorant of the law, thinking that you can wait until ‘ Article 24 ’ On the day of automatic abolition, there is really no need to join the group. "
She hopes to call for more people to reflect their opinions on Article 24 to NPC deputies and CPPCC members. She thinks these people have a say.
This self-proclaimed "old Wen Qing who once had a crush on Wilde" is now nicknamed "Mother Teresa" by group friends.
She positioned herself as a "night watchman" in this group, but she was also considered "too rational" by group friends, and even a bit like an "outsider".
But under the calm sea level, her fate is encountering an undercurrent. In 2013, her ex-husband left after she owed more than 3 million yuan in debt without her knowledge. The interest she bears is more than 500 yuan a day.
Today, her salary has been frozen and she has not received a penny for three months. Houses near Wudaokou have also been sealed up. She also suffers from malignant thyroid nodules and lives on the money lent to her by her sister.
"All my friends gradually left me when you ‘ Liabilities ’ Later, if you still have friends, you can only say that you haven’t been in debt long enough. " She told reporters with a smile, "In the end, everyone will be afraid that you are here to borrow money."
But she is not afraid to spend money on one thing. In order to lobby more NPC deputies and CPPCC members, her bag always contains more than 100 pages of materials criticizing Article 24. The important parts are all colored.
In order to get the price of printing a page for 35 cents, she will go to the nearby Tsinghua University campus to print, and a dozen will be 100 copies. The version is always updated, sometimes the old version of the material has not been distributed, and the new version has to be typed 100 copies.
She kept telling her friends that the only way to "practice the law" was "clumsy spirit", and there was no shortcut or "cake", "because ‘ Cake ’ It does not exist in itself. "
In her view, "the victim groups in history are doomed not to be tangible", but only to play the role of adhesive and concrete, bonding and condensing places that can really incite resources from all sides. "Let’s walk with our heads down together, and maybe walk out of the way."
The members of the group are indeed working "clumsily".
In order to contact a NPC deputy who is a doctor, someone asked someone to register and went to the doctor every week for two months.
After contacting the deputies to the National People’s Congress, some people wondered whether they should send a text message to remind them. As a result, they were caught in an inner struggle all day. When they received the reply, they were so excited that "the whole person was blinded".
Others still insist on mailing their handwritten letters to the judges of the court, telling them the harm of Article 24. The salary of one of the senders has been "executed" by the court, and he took out money from the living expenses of more than 1,000 yuan to send letters. He sent more than 1,000 letters in two years, and sent more than 120 letters in the most one day.
"This is the most humble expression when people are destroyed. The gesture of refusing to surrender to fate, although it can’t hold the throat of fate, at least means that individuals have not surrendered." Li Xiuping said.
Judge a "life" road
Li Xiuping once wrote to Wang Liren, a judge of the Intermediate People’s Court of Yichang City, Hubei Province, hoping that he would change the title of the article on "Article 24" in the past to "Judge a Way Out".
As one of the first judges to criticize Article 24, Wang Liren showed no mercy to Article 24. He called Article 24 "cancerous" and it was a "legal error at the national level".
In Wang Liren’s view, "Article 24" as a judicial interpretation and Article 41 of the Marriage Law are opposite or separated. The law says: "At the time of divorce, the debts originally incurred by the husband and wife living together should be paid jointly. If the joint property is insufficient to pay off, or if the property belongs to each other, it shall be paid off by mutual agreement; If the agreement fails, the people’s court shall make a judgment. "
Wang Liren explained to the China Youth Daily and Zhongqing Online reporter that in the case that one party is unwilling to repay the joint debt of husband and wife and the creditor does not bear the corresponding burden of proof, this leads to "the marriage relationship is a basket, and any debt is loaded inside."
In his view, the only way to really solve the problem is to abolish Article 24 and rebuild the rules through legal procedures. Or "case boycott", that is, when dealing with husband and wife debt cases, abandon or bypass the "Article 24" presumption rule, and apply Articles 41 and 19 of the Marriage Law, the principle of family agency and the fair rule of proof. This will make the "Article 24" exist in name only.
When Ma Xianxing, the current chief procurator of Yuhua District Procuratorate in Changsha, first learned about Article 24, he also recognized that it had "original sin".
At that time, he was still the president of the People’s Court of Ningxiang County. A grass-roots civil servant approached him and said that his ex-wife gambled in stocks and owed a lot of foreign debts, but he was constantly being taken to court. He was unable to repay a loan of 750,000 yuan.
The civil servant kept complaining, and the Hunan Higher People’s Court sent the case back for retrial, but the Ningxiang County People’s Court did not make a decision.
The opinion of the retrial collegiate bench of Ningxiang County Court is that "the loan amount is large and not used for family life, and it should be a personal debt of one spouse", but the president at that time did not agree to change the judgment.
Ma Xianxing went to the then president and asked her, "Is there a legal basis?"
The president took out "Article 24". When he saw that "it should be treated as a joint debt of husband and wife", he was extremely surprised.
"China has &lsquo since ancient times; It is difficult for an honest official to break housework ’ (saying), use ‘ Should ’ How can you be so hasty? " He went on reading, and he saw two "exceptional" situations stipulated in this judicial interpretation.
Later, he compared these two exceptions to "deaf ears", which have only decorative value. "This is not in line with the situation in our country at all."
He argued at that time that the case should be changed. The president reminded him that "this change will turn over." His answer is: turn over the plate and seek truth from facts.
He believes that because of the "Article 24", some judicial judges put aside the superior law and did not investigate the authenticity, legality and rationality of the creditor’s rights, and directly applied the "Article 24" mechanically.
Now, Ma Xianxing compares the issue of "Article 24" to the emperor’s new clothes. “‘ Article 24 ’ There have been so many problems, and some experts and scholars still say that there is no problem. The key is not to let go of face. " He said.
Li Xiuping knows better than anyone that no matter when Article 24 is amended, there will still be a group of people "falling before dawn", which is just a matter of the number.
More than once, she told the group of friends that she should go through all legal procedures and never let her case "die" like this. "As long as it can last until dawn, life may change."
In fact, many people’s property has been "executed". Many people are destined to live with huge debts for the rest of their lives. But when they called for the abolition of Article 24, they even worked harder than some people involved in the lawsuit.
A primary school teacher in Wuhan, when she first joined the group, just thought about how to solve her own case and consulted relevant experts. But when she looked at those people in the group who were framed by the "Twenty-four Articles" like herself, she thought that this was not her own business.
"Applicable ‘ Article 24 ’ There are more and more cases, which means there may be more victims inside. " She said.
Now she is in debt of one million yuan, with two children and living expenses of only 1,400 yuan a month.
The teacher said that there was "selfishness" in his efforts: "I hope my children will not be ‘ Article 24 ’ Frame it. Otherwise, I don’t trust her to get married. "
For Li Xiuping, who was alone, the sealed house was a kind of sustenance.
Every time she turns on the light after entering the door or locks the door before going out, she will think that she will be on the street in an instant.
Living in the shadow of "Article 24" for nearly four years, she described it as being in a long night that she could not choose.
Fellow travelers have told her that if Article 24 is abolished with everyone’s efforts, they still want to continue to do public welfare. But what she thinks is that she is actually not a person who likes to get together. "I hope that for the rest of my life, I will have the opportunity to return to the simple living method of hiding in a small building."